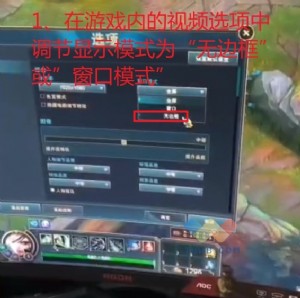
四台Cisco防火墙实现VPN网络
其实四台Cisco防火墙的VPN同两台防火墙做VPN没什么大的区别,只是一定要注意路由的配置(我就是在这上面花了很长的时间,不是多写就是少写了,多少都是不会通的);在四台Cisco pix做VPN中,有两种方式,一种是采用一个中心的方式,另一种就是分散式的(我自己起的名字J),前者,也就是说以一个PIX点为中心,其它的机器都连到本机上,在通过本机做路由;后者,则是在每一个路由上都要写出到另外三台的加密方式(听来就很麻烦),这里我采用的就是第一种类型(不是我偷懒,而是客户要求,谁让客户是上帝了呢!);
以下,是施工图以及四个Cisco pix的详细配置:
详细配置如下:
中心pix1:
: Saved
: Written by enable_15 at 23:10:31.763 UTC Thu Apr 24 2003
PIX Version 6.2(2)
nameif ethernet0 outside security0
nameif ethernet1 inside security100
enable password NHvIO9dsDwOK8b/k encrypted
passwd NHvIO9dsDwOK8b/k encrypted
hostname pixfirewall
fixup protocol ftp 21
fixup protocol http 80
fixup protocol h323 h225 1720
fixup protocol h323 ras 1718-1719
fixup protocol ils 389
fixup protocol rsh 514
fixup protocol rtsp 554
fixup protocol smtp 25
fixup protocol sqlnet 1521
fixup protocol sip 5060
fixup protocol skinny 2000
names
access-list 101 permit ip 172.17.0.0 255.255.0.0 172.16.0.0 255.255.0.0
access-list 101 permit ip 172.17.5.0 255.255.255.0 172.17.10.0 255.255.255.0
access-list 101 permit ip 172.17.10.0 255.255.255.0 172.17.5.0 255.255.255.0
access-list 101 permit ip 172.16.0.0 255.255.0.0 172.17.0.0 255.255.0.0
access-list 101 permit ip 172.17.5.0 255.255.255.0 172.17.17.0 255.255.255.0
access-list 101 permit ip 172.17.10.0 255.255.255.0 172.17.17.0 255.255.255.0
access-list hyzc permit icmp any any
access-list hyzc permit tcp any any
access-list hyzc permit udp any any
pager lines 24
interface ethernet0 auto
interface ethernet1 auto
mtu outside 1500
mtu inside 1500
ip address outside 192.168.0.2 255.255.255.240
ip address inside 172.17.5.1 255.255.255.0
ip audit info action alarm
ip audit attack action alarm
pdm history enable
arp timeout 14400
nat (outside) 1 0.0.0.0 0.0.0.0 0 0
nat (inside) 1 0.0.0.0 0.0.0.0 0 0
access-group hyzc in interface outside
route outside 0.0.0.0 0.0.0.0 218.7.16.49 1
route inside 172.17.0.0 255.255.0.0 172.17.5.20 1
route outside 172.17.17.0 255.255.255.0 192.168.0.4 1
route outside 172.17.16.0 255.255.255.0 192.168.0.1 1
route outside 172.16.0.0 255.255.255.0 192.168.0.3 1
route outside 172.17.18.0 255.255.255.0 218.7.16.52 1
route outside 172.17.18.64 255.255.255.0 218.7.16.49 1
route outside 218.7.248.100 255.255.255.252 218.7.16.49 1
timeout xlate 3:00:00
timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 rpc 0:10:00 h323 0:05:00 sip 0:30:00 sip_media 0:02:00
timeout uauth 0:05:00 absolute
aaa-server TACACS+ protocol tacacs+
aaa-server RADIUS protocol radius
aaa-server LOCAL protocol local
no snmp-server location
no snmp-server contact
snmp-server community public
no snmp-server enable traps
floodguard enable
sysopt connection permit-ipsec
no sysopt route dnat
crypto ipsec transform-set strong esp-des esp-sha-hmac
crypto map tohyjt 20 ipsec-isakmp
crypto map tohyjt 20 match address 101
crypto map tohyjt 20 set peer 192.168.0.3
crypto map tohyjt 20 set peer 192.168.0.4
crypto map tohyjt 20 set peer 192.168.0.1
crypto map tohyjt 20 set transform-set strong
crypto map tohyjt interface outside
isakmp enable outside
isakmp key cisco address 192.168.0.3 netmask 255.255.255.255
isakmp key cisco address 192.168.0.4 netmask 255.255.255.255
isakmp key cisco address 192.168.0.1 netmask 255.255.255.255
isakmp identity address
isakmp policy 9 authentication pre-share
isakmp policy 9 encryption des
isakmp policy 9 hash sha
isakmp policy 9 group 1
isakmp policy 9 lifetime 86400
telnet 218.7.16.49 255.255.255.255 inside
telnet 172.17.5.20 255.255.255.255 inside
telnet timeout 5
ssh timeout 5
terminal width 80
Cryptochecksum:8982919a8bfa10ba09cddee3f2da0e6a
: end
pix2配置:
: Saved
: Written by enable_15 at 00:00:48.042 UTC Fri Apr 25 2003
PIX Version 6.2(2)
nameif ethernet0 outside security0
nameif ethernet1 inside security100
enable password N.swjdczcTdUzgrS encrypted
passwd N.swjdczcTdUzgrS encrypted
hostname HYZCrc
fixup protocol ftp 21
fixup protocol http 80
fixup protocol h323 h225 1720
fixup protocol h323 ras 1718-1719
fixup protocol ils 389
fixup protocol rsh 514
fixup protocol rtsp 554
fixup protocol smtp 25
fixup protocol sqlnet 1521
fixup protocol sip 5060
fixup protocol skinny 2000
names
access-list 101 permit ip 172.17.17.0 255.255.255.0 172.17.10.0 255.255.255.0
access-list 101 permit ip 172.17.17.0 255.255.255.0 172.17.5.0 255.255.255.0
access-list hyzc permit icmp any any
access-list hyzc permit tcp any any
access-list hyzc permit udp any any
pager lines 24
interface ethernet0 auto
interface ethernet1 auto
mtu outside 1500
mtu inside 1500
ip address outside 192.168.0.4 255.255.255.252
ip address inside 172.17.17.254 255.255.255.0
ip audit info action alarm
ip audit attack action alarm
pdm history enable
arp timeout 14400
nat (outside) 1 0.0.0.0 0.0.0.0 0 0
nat (inside) 0 access-list 101
nat (inside) 1 0.0.0.0 0.0.0.0 0 0
route outside 0.0.0.0 0.0.0.0 218.7.37.5 1
timeout xlate 3:00:00
timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 rpc 0:10:00 h323 0:05:00 sip 0:30:00 sip_media 0:02:00
timeout uauth 0:05:00 absolute
aaa-server TACACS+ protocol tacacs+
aaa-server RADIUS protocol radius
aaa-server LOCAL protocol local
no snmp-server location
no snmp-server contact
snmp-server community public
no snmp-server enable traps
floodguard enable
sysopt connection permit-ipsec
no sysopt route dnat
crypto ipsec transform-set strong esp-des esp-sha-hmac
crypto map tohyzc 20 ipsec-isakmp
crypto map tohyzc 20 match address 101
crypto map tohyzc 20 set peer 192.168.0.2
crypto map tohyzc 20 set transform-set strong
crypto map tohyzc interface outside
isakmp enable outside
isakmp key cisco address 192.168.0.2 netmask 255.255.255.255
isakmp identity address
isakmp policy 9 authentication pre-share
isakmp policy 9 encryption des
isakmp policy 9 hash sha
isakmp policy 9 group 1
isakmp policy 9 lifetime 86400
telnet 172.17.17.253 255.255.255.255 inside
telnet timeout 5
ssh timeout 5
terminal width 80
Cryptochecksum:f63109daf8abcaf74a4f3b30ab01b48a
: end
pix3配置:
: Saved
:
PIX Version 6.0(1)
nameif ethernet0 outside security0
nameif ethernet1 inside security100
enable password X8QPBTnOSyX6X9Y9 encrypted
passwd X8QPBTnOSyX6X9Y9 encrypted
hostname pixfirewall
fixup protocol ftp 21
fixup protocol http 80
fixup protocol h323 1720
fixup protocol rsh 514
fixup protocol smtp 25
fixup protocol sqlnet 1521
fixup protocol sip 5060





 天下网吧·网吧天下
天下网吧·网吧天下