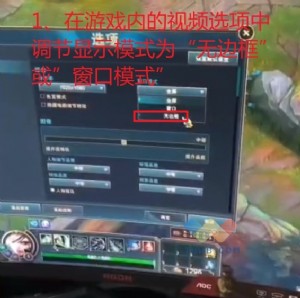
一个很有实用价值的QoS策略配置实例
某公司QoS策略配置实例
Current configuration : 3568 bytes
!
!
version 12.2
service timestamps debug datetime
service timestamps log datetime
service password-encryption
!
hostname xxxxxx
!
enable secret 5 $1$uJPt$/Uh
!
clock timezone China 8
ip subnet-zero
no ip source-route
ip cef
!
!
ip name-server x.x.x.x
ip name-server x.x.x.x
!
no ip bootp server
!
class-map match-any premium_class
description For premium
match protocol fasttrack
match protocol http
match protocol icmp
match protocol napster
match protocol netshow
match protocol pcanywhere
match protocol realaudio
match protocol streamwork
match protocol vdolive
match protocol cuseeme
match protocol telnet
match protocol secure-http
match access-group 110
match ip precedence 5
match ip precedence 4
match ip precedence 3
class-map match-any normal_calss
description For normal
match protocol ftp
match protocol imap
match protocol pop3
match protocol secure-ftp
match protocol secure-imap
match protocol secure-pop3
match protocol smtp
match access-group 120
match ip precedence 2
match ip precedence 1
!
!
policy-map qos_policy_map
class premium_class
bandwidth percent 50
random-detect
random-detect exponential-weighting-constant 4
police cir 2000000 bc 10000 be 10000
conform-action transmit
exceed-action transmit
class normal_calss
bandwidth percent 25
random-detect
random-detect exponential-weighting-constant 4
police cir 2000000 bc 2000 be 2000
conform-action transmit
exceed-action drop
!
!
!
!
interface FastEthernet0/0
ip address 192.168.0.1 255.255.255.0
ip address 192.168.1.1 255.255.255.0 secondary
ip access-group 130 in
ip verify unicast reverse-path
ip nat inside
ip route-cache same-interface
ip route-cache policy
ip policy route-map qos
duplex auto
speed auto
no cdp enable
!
interface Serial0/0
bandwidth 2048
ip address x.x.x.x 255.255.255.252
ip verify unicast reverse-path
no ip proxy-arp
ip nat outside
rate-limit input 2000000 20000 20000 conform-action transmit exceed-action drop
ip route-cache policy
service-policy output qos_policy_map
no cdp enable
!
ip nat inside source list 10 interface Serial0/0 overload
ip classless
ip route 0.0.0.0 0.0.0.0 x.x.x.x
ip route 192.168.0.0 255.255.255.0 192.168.1.1
ip route 192.168.1.0 255.255.255.0 192.168.0.1
no ip http server
no ip pim bidir-enable
!
!
access-list 10 remark NAT
access-list 10 permit 192.168.0.0 0.0.0.255
access-list 10 permit 192.168.1.0 0.0.0.255
access-list 110 remark normal
access-list 110 permit ip 192.168.0.0 0.0.0.255 any
access-list 120 remark premium
access-list 120 permit ip 192.168.1.0 0.0.0.255 any
access-list 130 remark anti BT and anti-virus
access-list 130 deny tcp any any range 6881 6890 time-range work
access-list 130 deny tcp any range 6881 6890 any time-range work
access-list 130 deny tcp any any range 6969 6979 time-range work
access-list 130 deny tcp any range 6969 6979 any time-range work
access-list 130 deny tcp any any range 7000 7100 time-range work
access-list 130 deny tcp any range 7000 7100 any time-range work
access-list 130 deny tcp any any range 9995 9996
access-list 130 deny tcp any range 9995 9996 any
access-list 130 deny tcp any any eq 5554
access-list 130 deny tcp any eq 5554 any
access-list 130 permit ip any any
no cdp run
route-map qos permit 10
match ip address 110
set ip precedence priority
!
route-map qos permit 20
match ip address 120
set ip precedence critical
!
banner motd ^CUnauthorized access will be Prosecuted!!!^C
!
line con 0
exec-timeout 0 0
line aux 0
line vty 0 4
password 7 121A0C0411045D5D7C
login
!
time-range work
periodic weekdays 8:30 to 18:00
!
!
end
公司有两个内网段:192.168.0.0/24,192.168.1.0/24。
192.168.0.0/24为低优先级内网段,192.168.1.0/24为高优先级内网段。
在class-map中premium_class类包括了192.168.1.0/24高优先级内网段,采用NBAR匹配实时性较高的应用如:napster、netshow、pcanywhere、realaudio、streamwork、vdolive、cuseeme、telnet等。
normal_class类包括了192.168.0.0/24低优先级内网段,采用NBAR匹配实时性不强的应用如:ftp、pop3、smtp等。
在policy-map中针对不同的class,采取不同的策略。如:CBWFQ、WRED等。因为公司互联网带宽为2M,故考虑WRED中的指数加权因子为4,最小阀值为5,最大阀值为17,标记几率分母为1。
在route-map(PBR)中采用匹配不同的ACL 110#,ACL 120#。设置不同的IP precedence值。
在F 0/0以太口上增加inbound policy--ACL 130#,在上班时间8:30到18:00禁止BT下载。限制震荡波病毒的端口。
在S 0/0串口上采用Input CAR策略。对进入S 0/0串口的流量进行整形。





 天下网吧·网吧天下
天下网吧·网吧天下